Hiding Secrets in Spontaneous Patterns
Embedding secret information in a seemingly ordinary image is one of the latest tricks in the world of cloak and dagger. A new technique for concealing messages in computer-generated images, described in Physical Review E, uses the mathematics of so-called pattern forming systems, such as spots on animals or the natural geographic clustering of vegetation. The encoded image is a random-looking mixture of stripes or dots that cannot be “unscrambled” by computer analysis because of the special properties of this class of equations. The technique’s inventors say their system could be the basis for highly secure communications in certain situations, but some experts in this field doubt the technique would be applicable in real covert operations.
The strategy of hiding messages in ordinary objects is called steganography. The advantage over cryptography is that it protects the sender and receiver by concealing the fact that communication is going on. Historical examples include messages written in invisible ink and secrets shrunken down into “microdots” that can replace periods in printed text. In today’s digital world, a message can be embedded in an image by modifying some of the ones and zeros in the binary code that assigns colors to the pixels. A human eye cannot detect the modification, but “steganalysis” programs often can, for example, by detecting a deviation in the usual statistical distribution of pixel shades.
To increase the security of digital image steganography, Loreta Saunoriene and Minvydas Ragulskis of Kaunas University of Technology in Lithuania explored whether the physics of self-organizing patterns could be used to better conceal messages. Self-organizing patterns were first observed in chemical reactions in which the chemical species spread out in a nonuniform way, forming stripes, spirals or other geometrical shapes. Similar patterns have been discovered in other so-called nonlinear systems, such as predator-prey interactions, where the patterns represent the clustering of animal species into specific regions.
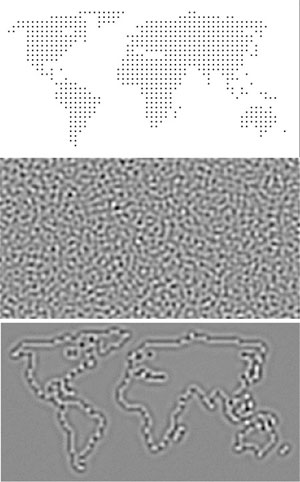
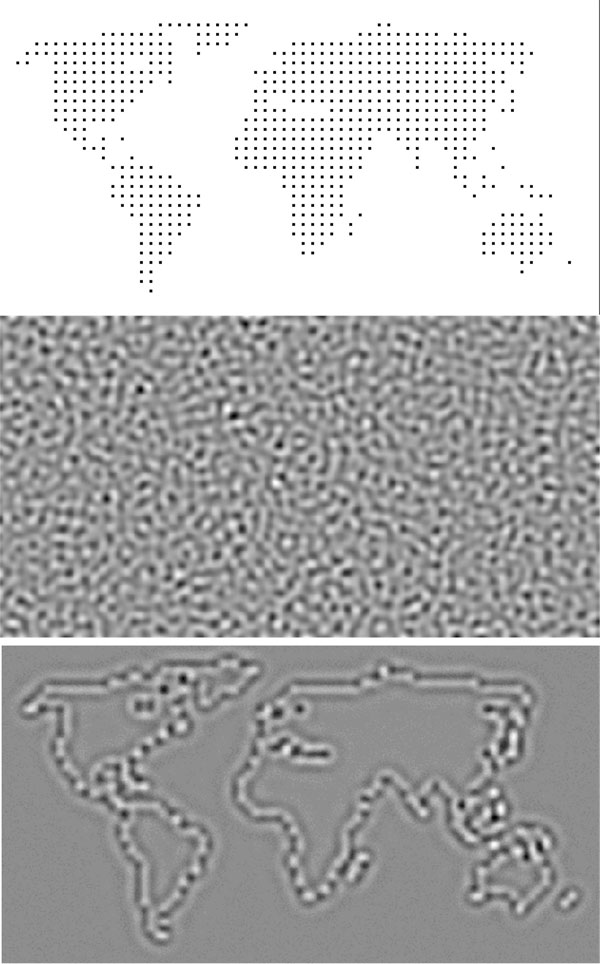
In their new technique, Saunoriene and Ragulskis use a particular algorithm from predator-prey models to diffuse, or “blur out,” an image so that it would be almost impossible to detect, even by image processing software. The researchers start with a noisy grayscale image—resembling the static or “snow” on an analog TV—that they generate with a mathematical formula. They then embed a secret message or picture by slightly brightening specific pixels to a degree that is imperceptible within the noise. Next, the researchers transform the image using repeated application of the predator-prey equations. Each iteration of the algorithm causes the information in the brightened pixels to diffuse outward. The diffusion is nonlinear, which means that the original pixel values can’t be retrieved by somehow reversing the diffusion process. As the pattern of irregular stripes and dots emerges, the original image is smoothed out to such an extent that a steganalysis program could detect nothing, Ragulskis says.
To decode the squiggly pattern, the recipient first generates the same noisy, “static” image and applies the same algorithm to it (all this math agreed upon in advance with the sender). Similar patterns form but without any message embedded inside. The recipient then subtracts this “blank template” pixel-by-pixel from the encoded image to get a blurry—but readable—version of the secret message.
Jessica Fridrich from the State University of New York in Binghamton thinks this is a “fascinating” idea, but the encoded images aren’t ordinary enough to avoid attention. “Unless most of us attach similar patterns to our emails (for some unknown reason), I would mark as potentially suspicious any email with such a pattern,” Fridrich says. Zoran Duric of George Mason University in Fairfax, Virginia, agrees and adds that messages based on low-resolution pictures or text have limited data capacity. Ragulskis counters that in some situations, transferring large amounts of data is not required—the point is to prevent others from recognizing that the pattern contains a secret message, even if they find it suspicious. The nonlinear algorithm wipes away any trace of hidden information, he says.
–Michael Schirber
Michael Schirber is a Corresponding Editor for Physics Magazine based in Lyon, France.
More Information
steganography review provided by Neil F. Johnson, a security consultant
“self-organization” from Scholarpedia
animations showing reaction-diffusion patterns by Arik Hagberg